Bynn Webhooks
Bynn's webhook system provides real-time notifications about verification events, enabling organizations to respond immediately to verification status changes and integrate seamlessly into their existing workflows. Webhooks eliminate the need for continuous polling and ensure that your systems receive instant updates when verification processes complete, encounter issues, or require additional attention through our enterprise-grade delivery infrastructure.
Webhook Architecture
The Bynn webhook system operates on an event-driven architecture that delivers HTTP POST requests to your specified HTTPS endpoints whenever significant verification events occur. Each webhook delivery includes comprehensive event data, verification context, and cryptographically signed metadata necessary for your application to process the notification securely and take appropriate action based on verification outcomes.
Webhook deliveries are engineered for maximum reliability and include sophisticated automatic retry mechanisms with exponential backoff for failed deliveries, ensuring that critical verification events reach your systems even during temporary network issues or endpoint unavailability. The webhook system maintains comprehensive delivery logs, performance analytics, and provides detailed insights about webhook performance, delivery success rates, and response time characteristics across your entire verification infrastructure.
The system supports both live production webhooks and sandbox testing webhooks through environment separation, allowing organizations to thoroughly test webhook integrations without affecting production data or triggering unintended business processes during development and integration phases.
Webhook Configuration
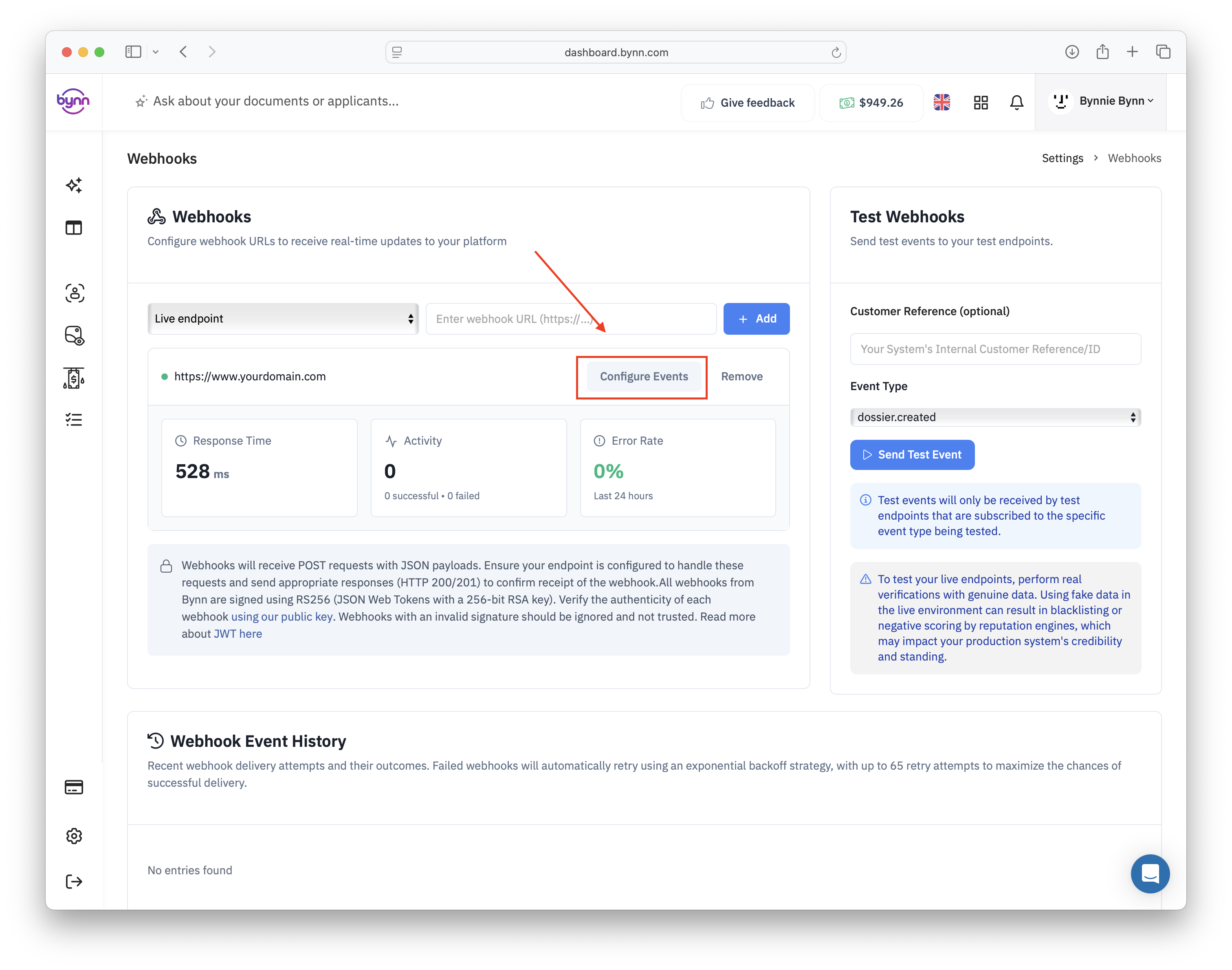
Configure Webhooks here: Webhook Settings
Endpoint Requirements
Webhook endpoints must be accessible via HTTPS to ensure secure delivery of sensitive verification data and maintain compliance with data protection regulations. Bynn enforces strict HTTPS requirements and validates SSL certificates to prevent man-in-the-middle attacks and ensure that webhook deliveries remain confidential during transmission. Endpoints must respond with HTTP status codes in the 200-299 range to indicate successful receipt of webhook data, with any other response codes triggering automatic retry mechanisms.
Response time requirements specify that webhook endpoints must respond within 10 seconds to prevent delivery timeouts and maintain efficient webhook processing throughput. Endpoints that consistently exceed response time limits may be automatically paused to prevent webhook queue buildup and ensure reliable delivery to responsive endpoints throughout the organization's webhook infrastructure.
Bynn's webhook system includes intelligent IP filtering that blocks private IP address ranges, localhost addresses, and specific cloud infrastructure ranges to prevent potential security vulnerabilities and ensure that webhook deliveries only reach legitimate external endpoints. This filtering includes comprehensive validation of destination addresses and prevents webhook delivery to internal network resources that could pose security risks.
Multiple Endpoint Management
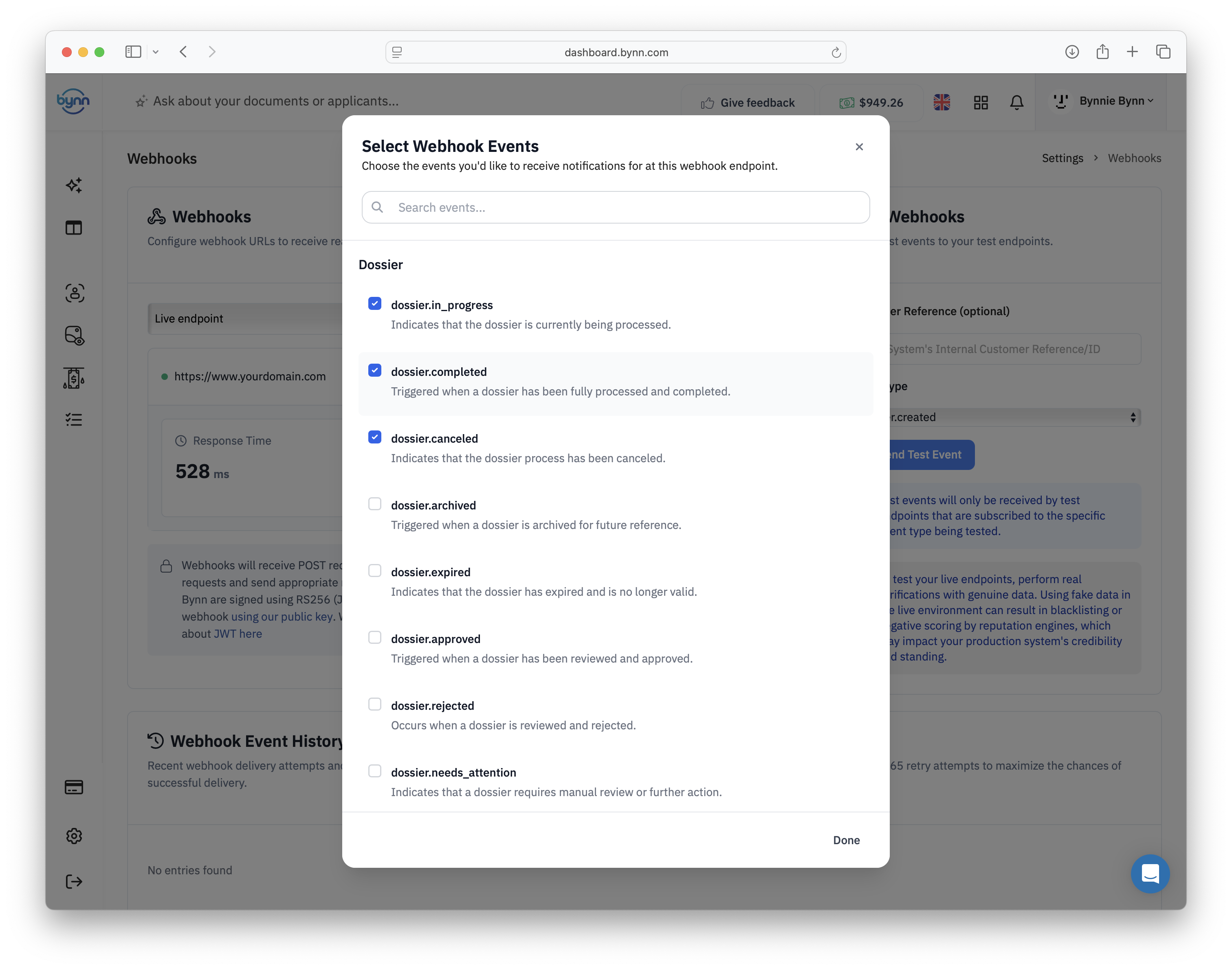
Organizations can configure and manage multiple webhook endpoints through the Bynn dashboard, with each endpoint supporting independent configuration settings including URL, HTTP method selection, retry parameters, and event subscription preferences. The dashboard provides comprehensive endpoint management tools including endpoint testing, performance monitoring, and delivery analytics that enable efficient webhook infrastructure management.
Each webhook endpoint maintains its own unique authentication token and signature validation parameters, ensuring that multiple endpoints can coexist securely without interfering with each other's authentication or delivery characteristics. Organizations can configure endpoint-specific retry behavior, timeout settings, and error handling preferences to optimize webhook delivery for different receiving systems and infrastructure requirements.
The endpoint management interface includes bulk configuration options for organizations managing large numbers of webhook endpoints, including template-based configuration, bulk event subscription management, and coordinated endpoint testing across multiple destinations simultaneously.
Advanced Security Features
Webhook security implementation includes multiple layers of protection designed to ensure authentic delivery and prevent unauthorized access to verification data. The primary security mechanism utilizes RS256 JWT signatures generated with RSA private keys, providing cryptographically strong authentication that enables webhook recipients to verify the authenticity and integrity of each webhook delivery.
Additional security headers include unique idempotency keys that prevent duplicate processing of webhook deliveries, webhook identification tokens that enable endpoint-specific processing logic, and test mode indicators that clearly identify sandbox webhook deliveries. The security implementation includes comprehensive request signing that covers both webhook headers and payload data, ensuring complete message integrity throughout the delivery process.
Organizations can implement additional security measures including webhook URL validation, request source verification, and payload encryption for sensitive verification data. The webhook system supports custom authentication headers and organization-specific security requirements while maintaining compatibility with standard webhook processing frameworks and libraries.
Sophisticated Retry Mechanisms
Webhook delivery failures trigger intelligent retry processing with sophisticated exponential backoff algorithms designed to balance delivery reliability with endpoint protection. The retry schedule begins with rapid retry attempts for transient failures including network timeouts and temporary service unavailability, followed by progressively longer intervals for persistent failures that may indicate endpoint configuration issues or extended service outages.
The default retry schedule includes immediate retry for the first failure, followed by retries at 1, 2, 4, 8, 16, and 32-minute intervals for the first six attempts. Subsequent retries occur hourly for attempts 6-10, then shift to 6-hour intervals for attempts 11-30, followed by daily retries for remaining attempts up to the configured maximum retry limit.
Organizations can customize retry behavior including maximum retry counts, retry interval progression, and failure threshold settings that determine when webhook endpoints are automatically paused due to persistent delivery failures. The retry system includes comprehensive logging and analytics that provide detailed insights into delivery patterns, failure causes, and endpoint performance characteristics.
Payload Structure and Event Data
Comprehensive Event Metadata
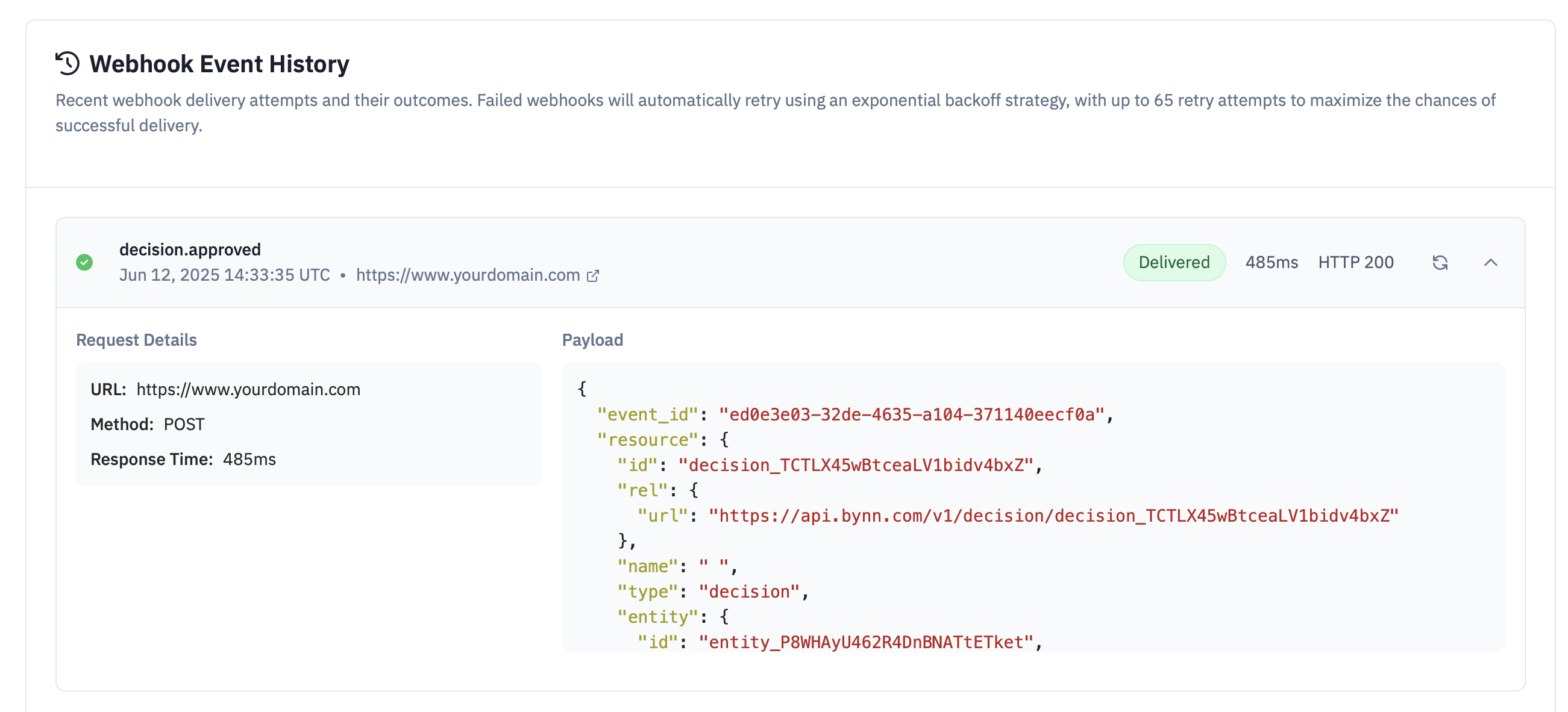
Each webhook payload includes extensive metadata about the verification event, including precise event type classification, ISO 8601 timestamps with UTC timezone specification, and unique event identifiers that enable proper webhook processing and deduplication. The metadata structure supports both automated webhook processing and detailed audit trail maintenance for compliance and operational monitoring purposes.
Event categorization follows a hierarchical naming structure that enables granular event filtering and routing. For example, document-related events include categories such as identity_document.approved, identity_document.rejected, and identity_document.analyzed, enabling organizations to implement specific processing logic for different document verification outcomes.
The event metadata includes comprehensive timing information including event generation timestamps, webhook delivery timestamps, and processing duration metrics that support performance monitoring and operational analytics. Organizations can use this timing data to optimize webhook processing performance and identify potential bottlenecks in verification workflows.
Detailed Verification Results
Webhook payloads include comprehensive verification result data that encompasses document analysis outcomes, biometric matching results, fraud detection insights, and overall verification decisions with supporting evidence and confidence scores. This detailed result data enables organizations to implement sophisticated decision-making logic and provide comprehensive audit trails for regulatory compliance and customer support purposes.
Document verification results include extracted customer data, document authenticity assessments, security feature validation outcomes, and fraud detection analysis with specific indicators and confidence levels. Biometric verification results provide facial matching confidence scores, liveness detection outcomes, and quality assessments that support risk-based authentication and fraud prevention workflows.
The verification data structure includes comprehensive metadata about processing methods, analysis confidence levels, and any manual review involvement, enabling organizations to implement appropriate processing logic based on verification quality and reliability characteristics.
Customer Data Integration
Customer information within webhook payloads includes structured personal data extracted from identity documents, biometric analysis results, and verification session metadata formatted for immediate integration into customer relationship management systems and onboarding workflows. The data structure follows consistent formatting standards that simplify database integration and customer record creation.
Personal data includes properly formatted names, addresses, date of birth information, and document numbers with appropriate data validation indicators and extraction confidence scores. This structured approach enables organizations to implement automated data validation and customer record creation while maintaining data quality and accuracy standards.
The customer data structure includes comprehensive privacy and consent tracking information that supports compliance with data protection regulations including GDPR, CCPA, and other regional privacy frameworks. Organizations can use this consent metadata to implement appropriate data handling and retention policies based on customer preferences and regulatory requirements.
Compliance and Audit Information
Webhook payloads include detailed compliance information that supports regulatory reporting, audit trail maintenance, and risk management processes. This compliance data encompasses jurisdiction-specific processing information, regulatory framework compliance confirmations, data localization details, and any additional compliance metadata relevant to specific verification scenarios.
Anti-Money Laundering screening results include comprehensive watchlist matching information, sanctions list checking outcomes, and adverse media screening results with detailed match confidence scores and recommended actions. This AML data enables organizations to implement immediate compliance workflows and risk management procedures based on screening outcomes.
Data processing location information includes specific geographic details about where customer data was processed and stored, supporting compliance with data residency requirements and regional data protection regulations. Organizations can use this location data for compliance reporting and audit documentation purposes.
Performance Monitoring and Analytics
Comprehensive Delivery Metrics
Bynn provides extensive webhook delivery analytics that enable organizations to monitor performance, identify optimization opportunities, and maintain reliable webhook processing infrastructure. The analytics system tracks delivery success rates, response time characteristics, retry frequency patterns, and error categorization across all webhook endpoints and event types.
Response time analytics include detailed measurements of webhook endpoint performance including average response times, 95th percentile response times, and response time distribution patterns over configurable time periods. Organizations can use this performance data to identify slow endpoints, optimize infrastructure capacity, and implement performance-based alerting systems.
Success rate monitoring provides granular insights into webhook delivery reliability including successful delivery percentages, failure rate trends, and correlation analysis between endpoint configuration and delivery success. The analytics system maintains rolling performance windows that enable trend analysis and performance regression detection across different time scales.
Advanced Error Analysis
Error categorization analytics provide detailed insights into webhook delivery failure patterns including network connectivity issues, endpoint timeout problems, HTTP error code distribution, and SSL certificate validation failures. This comprehensive error analysis enables organizations to implement targeted remediation strategies and proactive monitoring systems.
The error analysis system identifies systematic failure patterns that might indicate endpoint infrastructure issues, configuration problems, or capacity limitations. Organizations can use this analysis to implement preventive measures and optimize webhook endpoint reliability before failures impact critical business processes.
Retry pattern analysis provides insights into the effectiveness of retry mechanisms including retry success rates, optimal retry timing, and scenarios where manual intervention is required. This analysis enables organizations to optimize retry configuration for their specific infrastructure characteristics and business requirements.
Endpoint Performance Optimization
Webhook performance optimization involves comprehensive analysis of delivery patterns, endpoint response characteristics, and infrastructure utilization to identify improvement opportunities and ensure reliable high-volume processing. The optimization process includes endpoint configuration tuning, retry parameter adjustment, and infrastructure scaling recommendations based on actual usage patterns.
Performance optimization recommendations include endpoint-specific suggestions for timeout settings, retry configuration, and infrastructure improvements that can enhance webhook delivery reliability and reduce processing latency. Organizations can implement these recommendations to optimize webhook performance for their specific use cases and infrastructure requirements.
Advanced Integration Patterns
Enterprise Event-Driven Architecture
Bynn webhooks support sophisticated event-driven architecture patterns that enable organizations to implement complex business process automation and system integration workflows. These patterns include event routing, transformation, and aggregation capabilities that support enterprise-scale verification processing and downstream system integration.
Organizations can implement multi-system webhook distribution patterns where verification events trigger parallel processing across multiple business systems including customer relationship management platforms, compliance reporting systems, fraud detection tools, and business intelligence platforms. This parallel processing approach maximizes the value of verification data while maintaining system independence and fault tolerance.
Event filtering and routing capabilities enable organizations to implement sophisticated webhook processing logic that directs different event types to appropriate processing systems based on event characteristics, customer attributes, or business rules. This selective routing approach optimizes system resources and ensures that each system receives only relevant verification events.
High-Volume Processing Architecture
High-volume verification scenarios require specialized webhook processing architectures that can handle thousands of concurrent webhook deliveries while maintaining reliable processing and system performance. Bynn's webhook system supports these high-volume scenarios through optimized delivery algorithms, connection pooling, and intelligent load balancing across multiple endpoint infrastructure.
Queue-based processing architectures enable organizations to implement reliable webhook processing that can handle traffic spikes, system maintenance windows, and infrastructure scaling scenarios without losing verification events or impacting customer experience. These architectures include comprehensive retry mechanisms, dead letter queue handling, and performance monitoring capabilities.
Load balancing and redundancy patterns enable organizations to implement fault-tolerant webhook processing that continues operating even during partial infrastructure failures or maintenance activities. These patterns include multiple endpoint configuration, failover processing, and automated endpoint health monitoring capabilities.
Compliance and Audit Integration
Webhook integration for compliance and audit purposes requires specialized processing patterns that maintain comprehensive audit trails, ensure data integrity, and support regulatory reporting requirements. Bynn's webhook system provides detailed audit metadata and compliance tracking information that supports these specialized integration requirements.
Audit trail integration patterns enable organizations to implement comprehensive verification event logging that meets regulatory requirements for financial services, healthcare, and government applications. These patterns include tamper-evident logging, long-term data retention, and compliance reporting automation capabilities.
Regulatory reporting automation patterns leverage webhook data to populate compliance reporting systems automatically, ensuring that verification events are captured in appropriate regulatory frameworks without manual intervention. These patterns support multiple regulatory requirements including AML reporting, data protection compliance, and industry-specific regulations.
Updated 8 months ago