Document Fraud Detection
Bynn's Document Fraud Detector employs advanced forensic analysis to identify fraudulent documents and sophisticated forgeries. This multi-layered detection system combines AI-powered analysis, metadata examination, and database verification to ensure document authenticity.
Document fraud represents one of the most significant challenges in identity verification. Fraudsters use increasingly sophisticated techniques including digital manipulation, template-based generation, and AI-created content to create convincing fake documents.
Detection Philosophy:
Bynn's approach combines multiple detection methodologies to create a comprehensive fraud detection system. No single method can catch all fraud attempts, but layering multiple detection techniques creates a robust defense against even sophisticated attacks.
Multi-Layer Analysis:
The system analyzes documents from multiple perspectives including content analysis, metadata examination, version history, embedded codes, digital signatures, and database verification. Each layer provides different insights into document authenticity.
Core Detection Modules
🤖 AI-Powered Document Analysis
Purpose: Advanced AI analysis for document content verification and fraud detection.
The AI analyzer examines document content to identify inconsistencies, validate structure, and detect fraud patterns that may not be visible to human reviewers.
Content Classification:
The system identifies document types and validates their structure against known templates. This helps detect documents that claim to be one type but have the structure of another.
Consistency Verification:
Advanced algorithms cross-reference AI-extracted dates with metadata timestamps, verify mathematical consistency in financial documents, and analyze text patterns for suspicious alterations.
Fraud Pattern Detection:
Machine learning models trained on known fraud patterns identify suspicious elements like inconsistent fonts, irregular spacing, or text that appears artificially generated.
📊 Metadata Analysis
Purpose: Comprehensive examination of document metadata and creation history.
Document metadata contains valuable information about how and when documents were created. This invisible data often reveals fraud attempts that appear legitimate on the surface.
PDF Metadata Examination:
The system analyzes PDF metadata to identify creation tools, detect edit history, validate producer and creator information, and identify temporal anomalies in creation and modification dates.
EXIF Data Analysis:
For image-based documents, EXIF data reveals camera information, editing software usage, GPS location data, and timestamp information. Inconsistencies in this data often indicate manipulation.
Tool Attribution:
The system maintains a database of software signatures and can identify when documents have been edited with suspicious tools or show signs of professional manipulation software usage.
🔄 PDF Version Analysis
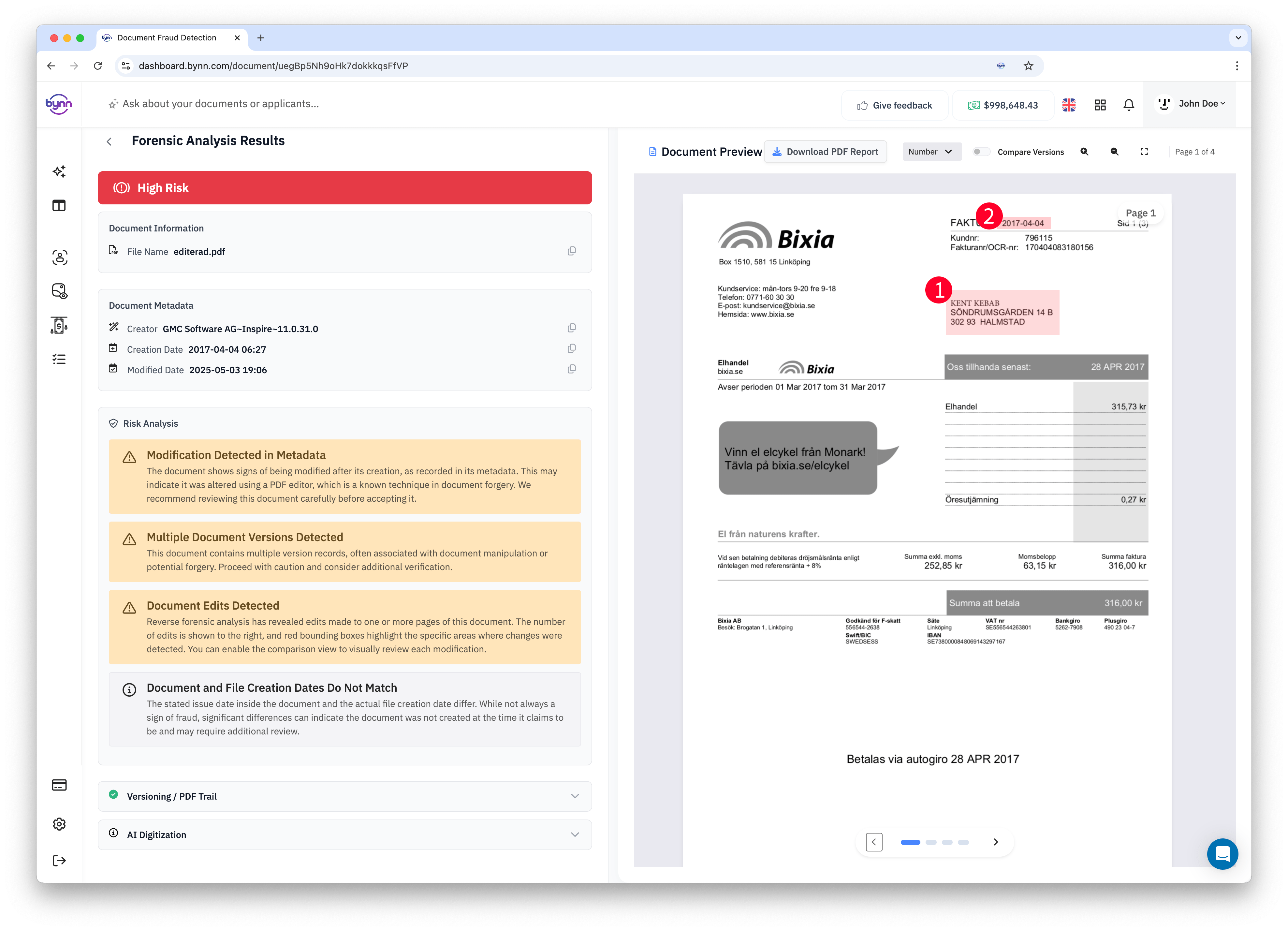
Purpose: Advanced PDF version analysis to detect hidden modifications.
PDF Version technology recovers all versions of a PDF document, even when changes appear to have been permanently applied. This reveals the complete editing history and highlights areas of modification.
Version Recovery:
The system extracts all historical versions of PDF documents, identifying what content was added, modified, or deleted at each stage of editing.
Visual Comparison:
Pixel-level comparison between document versions reveals even subtle modifications. The system can highlight exact areas where changes occurred.
Edit Visualization:
Results include visual representations showing what parts of documents have been modified, helping reviewers understand the nature and extent of any alterations.
🏷️ Barcode & Code Analysis
Purpose: Extraction and validation of embedded codes and barcodes.
Many legitimate documents contain embedded barcodes or QR codes with encoded information. These codes can be validated against the visible document content and external databases.
Code Processing:
The system extracts and processes QR codes, PDF417 barcodes (common on government IDs), Data Matrix codes, and other embedded information carriers.
Cross-Validation:
Extracted code data is compared with visible document information to identify discrepancies. For example, a driver's license barcode should contain information matching the printed text.
Government Integration:
For supported countries like India, the system can validate QR codes against government databases through Goverlink integration, providing authoritative verification.
🔐 Digital Signature Verification
Purpose: Cryptographic validation of document authenticity.
Digital signatures provide cryptographic proof of document authenticity and integrity. The system validates these signatures against trusted certificate authorities.
Certificate Validation:
The system verifies certificate chains back to trusted root authorities, ensuring signatures come from legitimate sources.
Integrity Verification:
Cryptographic validation confirms that signed documents haven't been altered since signing. Any modification breaks the signature and indicates tampering.
Timestamp Validation:
Digital timestamps are validated to ensure documents were signed when claimed, preventing backdating or other temporal fraud attempts.
🎯 AI Deepfake & Generation Detection
Purpose: Cutting-edge detection of AI-generated or manipulated content.
As AI technology advances, fraudsters increasingly use AI tools to generate fake documents or manipulate existing ones. Bynn's detection system identifies these artificial creations.
Generation Detection:
Machine learning models analyze documents for signs of AI generation, including unnatural text patterns, synthetic image elements, and algorithmic artifacts.
Deepfake Identification:
Advanced algorithms detect when photos within documents have been manipulated using deepfake or face-swapping technology.
Confidence Scoring:
The system provides confidence scores indicating the likelihood that content is artificially generated, helping reviewers prioritize manual inspection.
🚫 Blacklist & Dataset Verification
Purpose: Real-time verification against fraud databases.
The system maintains comprehensive databases of known fraudulent documents, compromised account numbers, and suspicious patterns to provide immediate identification of previously seen fraud.
Document Verification:
Known fraudulent document numbers, templates, and patterns are checked against incoming documents to identify repeat fraud attempts.
Financial Validation:
Bank account numbers, IBAN codes, and routing numbers are validated against databases of known fraudulent or closed accounts.
Global Intelligence:
Integration with international fraud databases provides worldwide coverage of known fraud patterns and compromised credentials.
Fraud Detection Workflow
Document Processing Pipeline:
When a document is uploaded, it immediately enters the fraud detection pipeline where multiple analysis modules run in parallel to maximize efficiency.
graph TD
A[Document Upload] --> B[Metadata Extraction]
A --> C[AI Content Analysis]
A --> D[Barcode Extraction]
B --> E[Edit Tool Detection]
B --> F[Version Analysis]
C --> G[Content Validation]
C --> H[Fraud Pattern Detection]
D --> I[Code Verification]
E --> J[Risk Assessment]
F --> J
G --> J
H --> J
I --> J
J --> K[Forensic Score]
K --> L[Decision Engine]
style A fill:#e1f5fe
style L fill:#e8f5e8
style J fill:#fff3e0
Analysis Coordination:
Different detection modules analyze various aspects of the document simultaneously. Results are then combined to create a comprehensive risk assessment.
Risk Scoring:
Individual module results are weighted and combined to produce an overall fraud risk score from 0-100, with higher scores indicating greater fraud likelihood.
Evidence Collection:
The system collects visual evidence of detected issues, creates detailed reports of findings, and provides specific indicators that triggered fraud alerts.
Advanced Detection Capabilities
Sophisticated Fraud Detection:
Bynn's system can identify advanced fraud techniques including photo substitution in identity documents, text alterations in financial statements, entirely fabricated documents, digital watermark removal, and template-based document generation.
Tool Detection:
The system identifies when documents have been edited with specific tools including Adobe Acrobat/Photoshop, online PDF editors like SmallPDF and ILovePDF, photo editors like Photopea and Pixlr, document processors like Microsoft Word, and suspicious modification tools.
Pattern Recognition:
Machine learning models continuously learn from new fraud patterns, improving detection capabilities as new fraud techniques emerge.
Results and Reporting
Comprehensive Output:
Fraud detection results include an overall risk score with detailed breakdown, individual module results with confidence levels, visual evidence highlighting detected modifications, tool attribution identifying software used for editing, version history showing document evolution, and fraud indicators with specific risk classifications.
Visual Evidence:
When modifications are detected, the system provides visual highlighting of altered areas, side-by-side comparisons of document versions, and clear indicators of what specific changes were made.
Actionable Intelligence:
Results are designed to help compliance teams make informed decisions about document authenticity and provide clear evidence for manual review when needed.
Integration with Verification Workflow
Automatic Processing:
Document fraud detection runs automatically as part of the verification workflow, requiring no additional configuration or manual intervention.
Decision Engine Integration:
Fraud detection results feed into Bynn's decision engine, where they are combined with other verification factors to make final acceptance decisions.
Manual Review Triggers:
High fraud risk scores automatically trigger manual review workflows, ensuring that suspicious documents receive human attention.
Customizable Thresholds:
Organizations can configure fraud detection sensitivity levels and auto-rejection thresholds based on their risk tolerance and business requirements.
Updated 8 months ago